A team of researchers from the University of Buffalo, located in the well-known city of New York, has managed to reveal how easy it can be to hack a 3D printer nowadays thus highlighting the danger of the theft of intellectual property from 3D printing. Without a doubt, at least that's how I personally think, 3D printing has the potential to literally change the world, although for this, especially in terms of security, much more work must be done.
You have to think that today you only need a 3D model to create a product, something that can encourage many companies to achieve access to our systems to get hold of these files and thus be able to benefit from all the investment that our company has made in research and development. Something that seems very complicated has just been revealed by the team of researchers led by Professor Wenyao Xu PhD.
In statements of the professor Wenyao:
Many companies are hard at work on 3D printing trying to revolutionize business, but there is still a great lack of safety knowledge related to these machines, leaving intellectual property completely vulnerable.
From the University of Buffalo they warn us of the little security implemented in current 3D printers
Normally, companies tend to protect this kind of files through encryption, watermarks or simply through an alarm system, protection that can usually be broken using force but, on that occasion, the team of researchers has managed to show that no need to break the system to steal information.
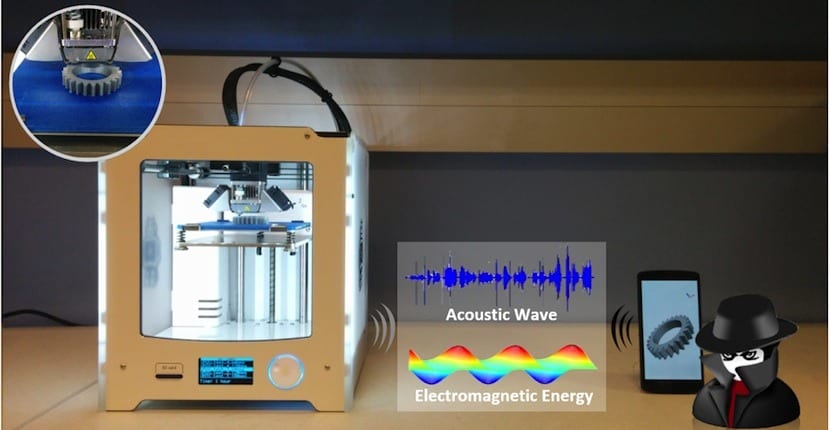
The work has been done by creating a specific app that would be executed by a smartphone. This app was in charge of measuring the acoustics and electromagnetic waves generated by the 3D printer during the process of creating a specific part. Once all this process has been recorded, through reverse engineering, it has been possible to know the location of the nozzle and even see what is being printed completely.
At the moment this process is not perfect, even when placing the smartphone very close to the machine. The team has only managed to reproduce a piece with an accuracy of 94%, which is reduced to 90% if the piece is too complex. As the terminal is separated from the machine, this precision will also be reduced. Even so, a trusted employee of any company could easily have access to the printing system which would open the doors to industrial espionage.